5 important rules to prevent cybercriminals from fooling you
Categories: Life hacks | Microworld | Science | Technology | World
By Vika https://pictolic.com/article/5-important-rules-to-prevent-cybercriminals-from-fooling-you.htmlIn the age of information technology, security is very important. Important personal information in our lives can be used to make money. Today hackers are not only very experienced computer users but also good psychologists. In order not to be deceived, you need to know what information can be shared and what information must be kept confidential.
Pictolic collects a few tips that everyone should know to keep their information safe.
5 PHOTOS
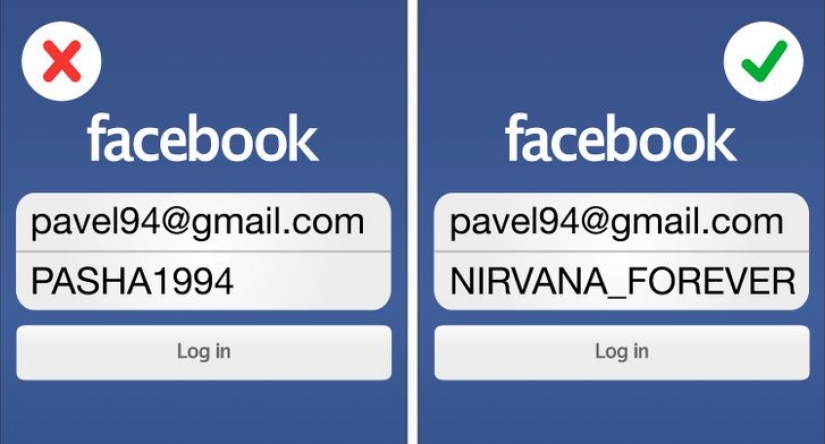
1. Create cognitive passwords.
Many people use the same password for completely different sources, both business and personal. Some people think it is possible to change some characters, but they leave the password database as it is. It's not safe at all. Cybercriminals use password dictionaries to help them hack you. Passwords must be complex. If you are afraid that you will forget all passwords due to their large number, you can use a password manager or create your own algorithm or method. Better to use a "non-standard" password. Neither the date of birth nor, for example, the name of your favorite character in the password. Use association instead. For example, use the first letter of your favorite song with your other favorite characters. A hacker cannot find such a password in his dictionary. Better yet, use an online password generator that will create a password for you using special characters.

2. Do not cover the webcam.
According to security experts, there is no point in covering your webcam. Although the personal webcam can be tracked, in most cases cybercriminals do not use this method. What do they see? Watching videos for hours is difficult and expensive.

3. Be aware of the danger over your shoulder.
Criminals often use the old school method: they look over our shoulders and look at the data we enter in public places. To avoid this threat, you can use special screens to prevent other people from seeing anything on your device. And, of course, you need to be especially careful when entering data to access any account.

4. Use the 3-2-1 rule.
To avoid losing valuable information due to an online attack, use the 3-2-1 rule. Losing your information can be costly. If a hacker finds your computer, at least you will have the information in the database. The rules are as follows:
You have at least 3 copies (original and two copies).
You are using a different type of storage (hard drive and cloud service).
At least one copy is kept elsewhere.
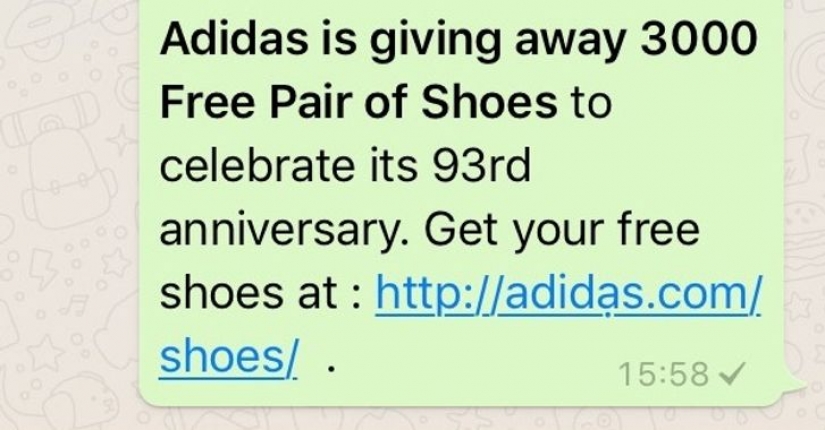
5. Pay attention to the addresses.
If you take a close look at the screenshot, you can see how important it is to pay attention to detail. The address looks familiar, but if you look at it, you will see a dot under the second letter "a". If you don't notice, you will follow a link that will take you to a dangerous website or send a virus to your smartphone, tablet, or computer.
Keywords: People | Technology | Microworld | Information | Money | Robber | Hack | Hacker | Lifehacks | Cyber | Cybercriminals | Criminal | Rules | Computer | Network
Post News ArticleRecent articles

It's high time to admit that this whole hipster idea has gone too far. The concept has become so popular that even restaurants have ...

There is a perception that people only use 10% of their brain potential. But the heroes of our review, apparently, found a way to ...
Related articles

This is an amazing photo project of Mike Harvey: it takes people in his car, and photographs them at the same time, we are about to ...

Surely, many of you had classmates who, to put it mildly, were not distinguished by outstanding external data. Braces, strange ...

Yes, Pets benefit our health and it is proven by science. Their very existence certainly makes us happier, but also prolongs life. ...

New Year's is a time to surprise and delight loved ones not only with gifts but also with a unique presentation of the holiday ...